[CKA] Secret 운영
Secret 이란?
- key:value 타입으로 데이터 저장
- 데이터가 BASE64로 인코딩된 ASCII text가 들어감
- Binary Data는 ASCII text로 변환되어 BASE64로 인코딩 되어 저장
- BASE64는 암호화가 아님
※ base64 확인
# echo "a" | base64
YQo=
# echo "YQo=" | base64 -d
a
[문제]
Create a kubernetes secret and expose using a file in the pod.
1. Create a kubernetes Secret as follows:
- Name : super-secret
- DATA : password=secretpass
2. Create a Pod named pod-secrets-via-file, using the redis image, which mounts a secret named super-secret at /secrets.
3. Create a second Pod named pod-secrets-via-env, using the redis image, which exports password as PASSWORD
[풀이]
1. Secret 생성
- docs의 Secret 생성 참고
https://kubernetes.io/docs/concepts/configuration/secret/#use-cases
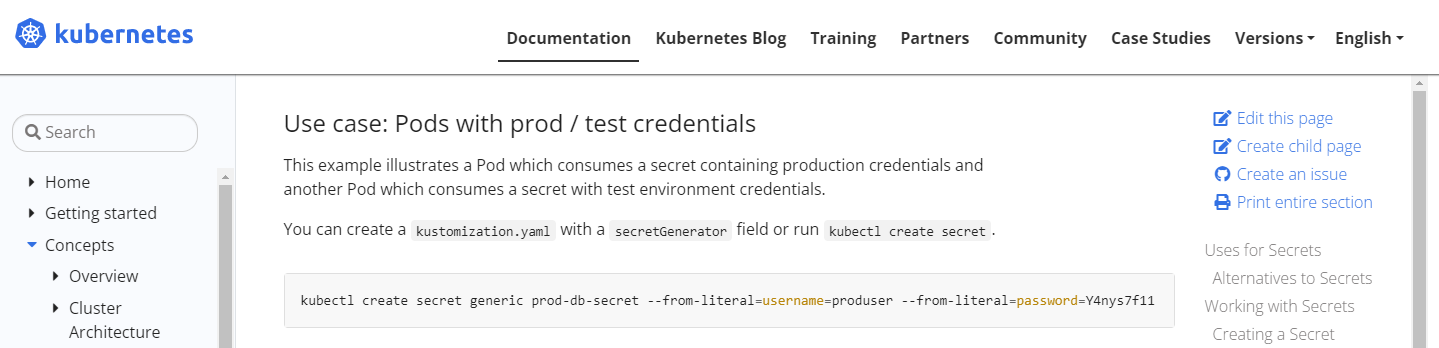
- Secret 생성 후 확인
# kubectl create secret --help
Create a secret using specified subcommand.
Available Commands:
docker-registry Create a secret for use with a Docker registry
generic Create a secret from a local file, directory, or literal value
tls Create a TLS secret
Usage:
kubectl create secret [flags] [options]
Use "kubectl <command> --help" for more information about a given command.
Use "kubectl options" for a list of global command-line options (applies to all commands).
# kubectl create secret generic super-secret --from-literal=password=secretpass
# kubectl get secrets
NAME TYPE DATA AGE
super-secret Opaque 1 10s
ttabae-secret Opaque 2 101d
# kubectl describe secrets super-secret
Name: super-secret
Namespace: default
Labels: <none>
Annotations: <none>
Type: Opaque
Data
====
password: 10 bytes
# kubectl get secrets super-secret -o yaml
apiVersion: v1
data:
password: c2VjcmV0cGFzcw==
kind: Secret
metadata:
creationTimestamp: "2023-04-01T09:39:39Z"
name: super-secret
namespace: default
resourceVersion: "297219"
uid: 2814a20f-7016-403e-af50-0858fd017cd9
type: Opaque
2. pod-secrets-via-file Pod 생성
- docs의 Secret pod 생성 참고
https://kubernetes.io/docs/concepts/configuration/secret/#using-secrets-as-files-from-a-pod
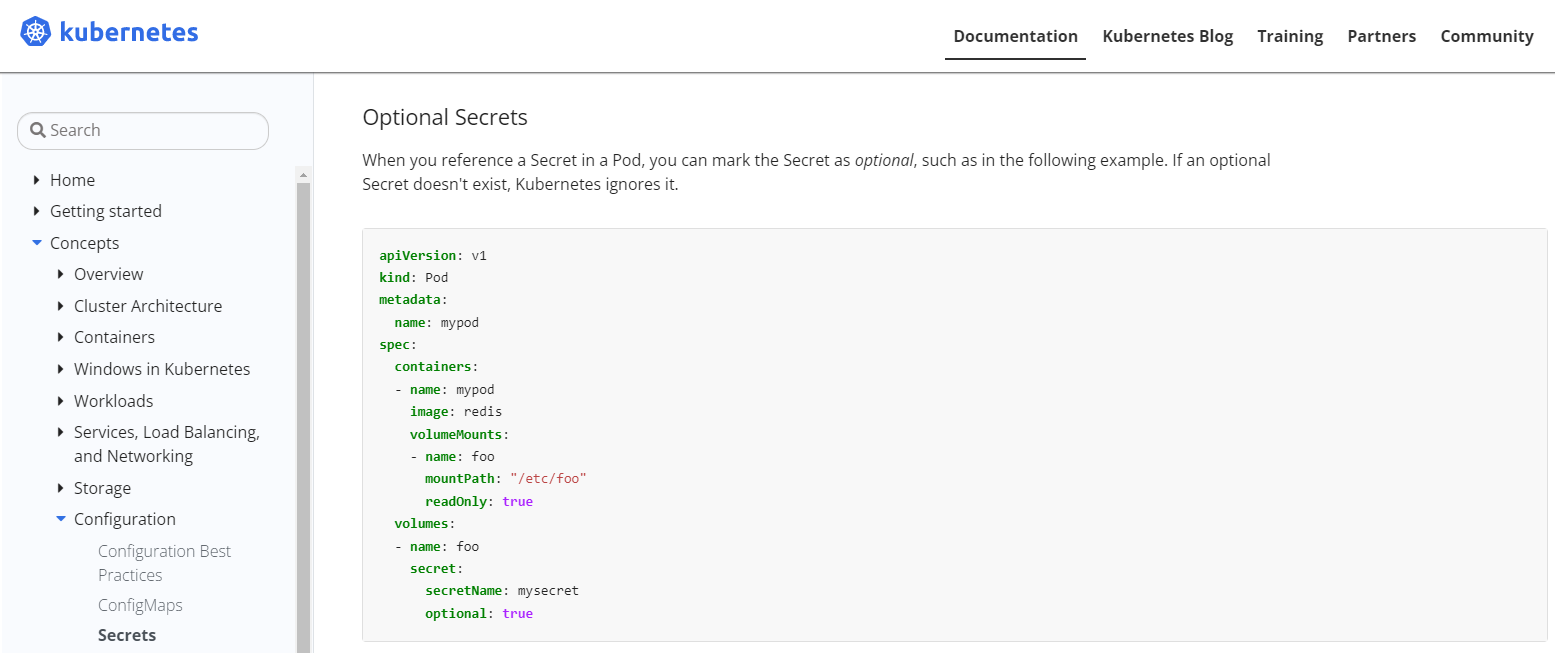
- pod 생성 후 volume mount 된 설정에서 password 확인
# cat pod-secrets-via-file.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod-secrets-via-file
spec:
containers:
- name: mypod
image: redis
volumeMounts:
- name: foo
mountPath: "/secrets"
readOnly: true
volumes:
- name: foo
secret:
secretName: super-secretroot
# kubectl apply -f pod-secret-via-file.yaml
# kubectl get pod
# kubectl exec -it pod-secrets-via-file -- ls /secrets
password
# kubectl exec -it pod-secrets-via-file -- cat /secrets/password
secretpassroot
3. pod-secrets-via-env Pod 생성
- docs의 Secret 환경변수 참고
https://kubernetes.io/ko/docs/concepts/configuration/secret/
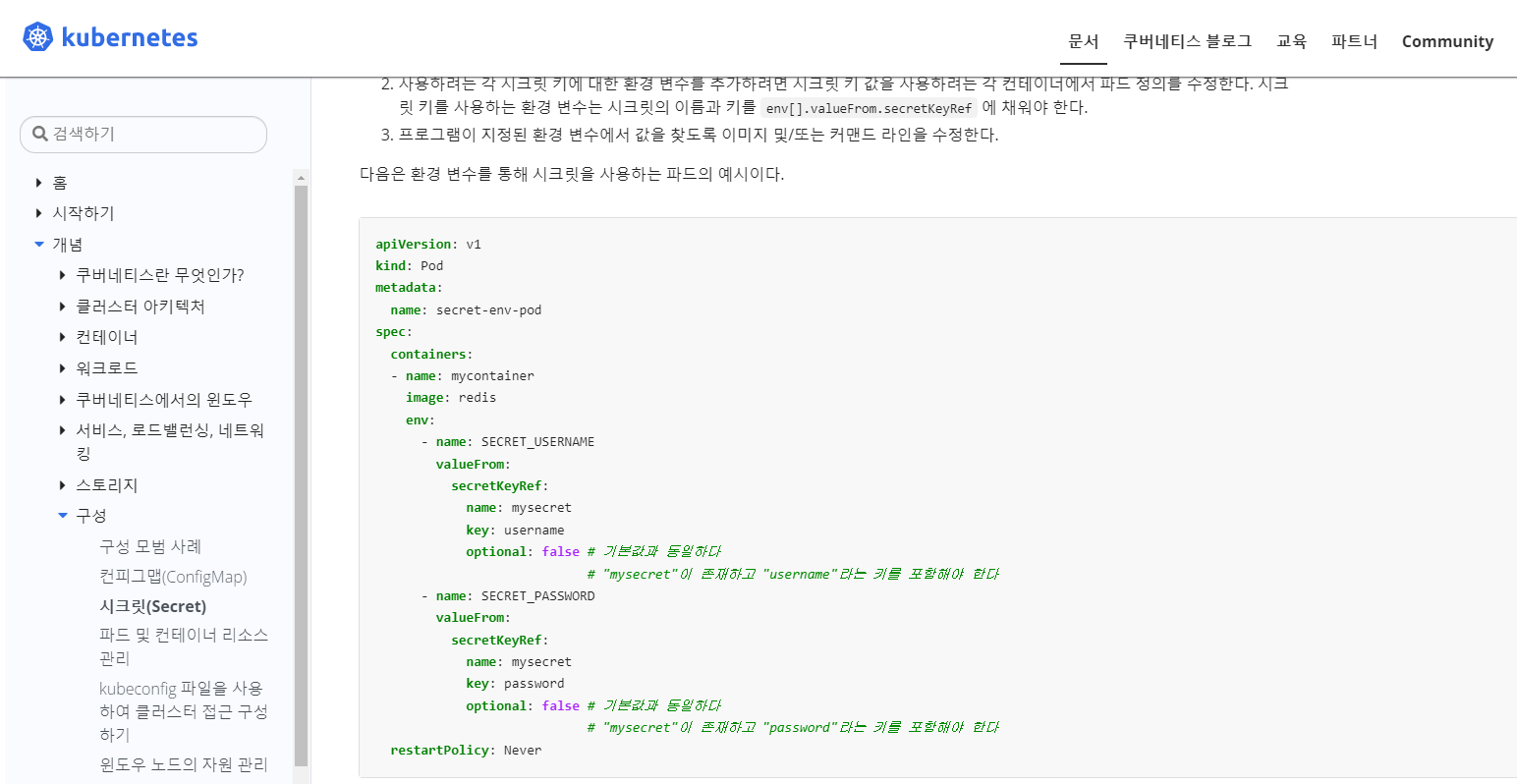
- pod 생성 후 env 확인
# cat pod-secrets-via-env.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod-secrets-via-env
spec:
containers:
- name: mycontainer
image: redis
env:
- name: PASSWORD
valueFrom:
secretKeyRef:
name: supser-secret
key: password
# kubectl apply -f pod-secrets-via-env.yaml
# kubectl get pod pod-secrets-via-env
# kubectl exec pod-secrets-via-env -- env
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
HOSTNAME=pod-secrets-via-env
GOSU_VERSION=1.16
REDIS_VERSION=7.0.10
REDIS_DOWNLOAD_URL=http://download.redis.io/releases/redis-7.0.10.tar.gz
REDIS_DOWNLOAD_SHA=1dee4c6487341cae7bd6432ff7590906522215a061fdef87c7d040a0cb600131
PASSWORD=secretpass
KUBERNETES_SERVICE_PORT=443
KUBERNETES_SERVICE_PORT_HTTPS=443
KUBERNETES_PORT=tcp://10.96.0.1:443
KUBERNETES_PORT_443_TCP=tcp://10.96.0.1:443
KUBERNETES_PORT_443_TCP_PROTO=tcp
KUBERNETES_PORT_443_TCP_PORT=443
KUBERNETES_PORT_443_TCP_ADDR=10.96.0.1
KUBERNETES_SERVICE_HOST=10.96.0.1
HOME=/root
[참고]
- 유투브 따배씨